It’s not as difficult as it would seem to implement AES encryption in PHP. The OpenSSL extension that comes with PHP takes care of the majority of the work, saving you from having to start from scratch with cryptography. The secret is to know what you’re doing and steer clear of typical blunders that could expose your info.
It takes more than just running a few functions to get AES encryption right. Consider key creation, selecting the appropriate encryption mode, managing initialization vectors appropriately, and ensuring that your encrypted data is impenetrable. You might as well be keeping your private information in plain text if you forget any of these components.
This simple tutorial demonstrates how to create a reliable, basic AES implementation with PHP’s built-in features and security procedures that are effective in real-world settings.
The Advanced Encryption Standard (AES) is a symmetric block cipher that processes data in 128-bit blocks. Based on the Rijndael cipher, AES performs multiple transformation rounds on each block through four main operations: SubBytes (S-box substitution), ShiftRows (cyclic shifts), MixColumns (matrix multiplication), and AddRoundKey (combining with round keys).
AES supports three key lengths: 128, 192, and 256 bits. AES-256 provides the strongest security for critical applications. The algorithm offers proven resistance against brute-force and side-channel attacks when properly implemented with appropriate modes and integrity verification. Modern implementations often use Galois/Counter Mode (GCM) to provide both confidentiality and authentication in a single operation.
Before implementing AES encryption, ensure your PHP environment has the OpenSSL extension properly configured. Most modern PHP installations include OpenSSL by default, but verification is essential for secure implementation.
Check if OpenSSL is available in your PHP environment using these verification methods:
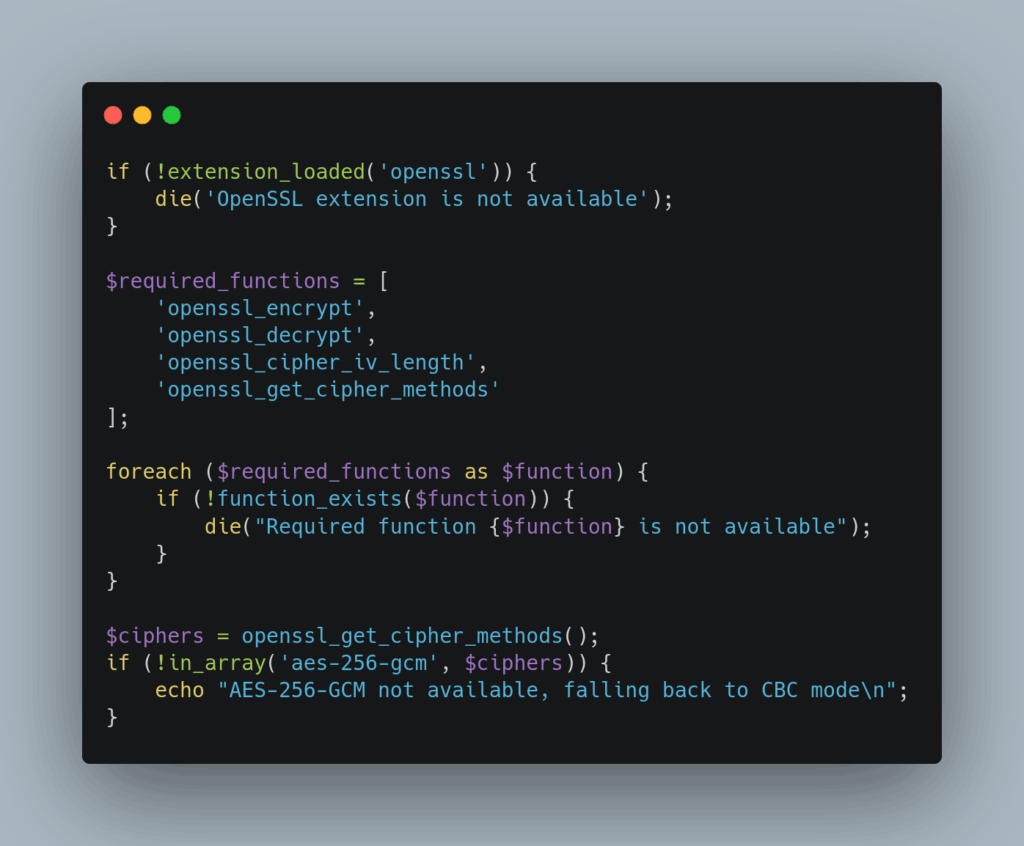
If OpenSSL is missing from your installation, the setup process varies by operating system:
For Ubuntu/Debian systems, install the required packages using apt-get install php-openssl openssl. CentOS/RHEL users should run yum install php-openssl openssl-devel. Windows users typically need to uncomment the OpenSSL extension line in php.ini and ensure the required DLL files are present.
After installation, restart your web server and verify the extension loaded correctly using php -m | grep openssl or by checking phpinfo() output.
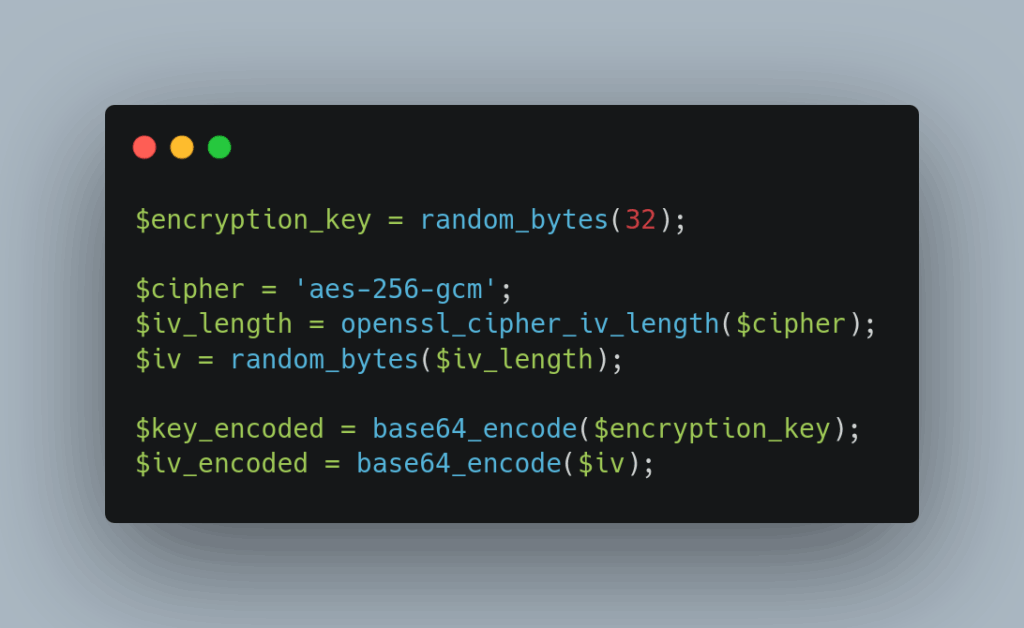
Cryptographically secure key and IV generation forms the foundation of any secure encryption system. PHP provides several functions for generating random data, but you must use the appropriate ones for cryptographic purposes.
Use random_bytes() for all cryptographic random data generation, as it provides cryptographically secure pseudorandom bytes suitable for encryption keys and initialization vectors:
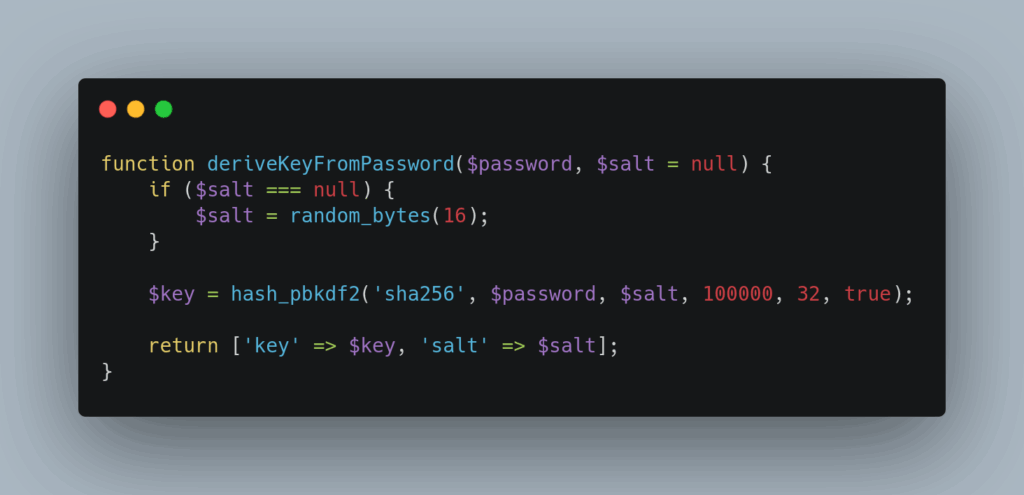
When deriving keys from user passwords, implement proper key derivation functions with sufficient iterations and random salts:
Never reuse initialization vectors across different encryption operations, as this compromises security. Generate fresh IVs for each encryption session and store them alongside the ciphertext for decryption.
Your choice of AES operation mode significantly impacts both security and performance. Modern applications should prioritize authenticated encryption modes that provide both confidentiality and integrity protection.
AES-GCM (Galois/Counter Mode) represents the current best practice for new applications. It provides authenticated encryption, combining confidentiality and integrity verification in a single operation:
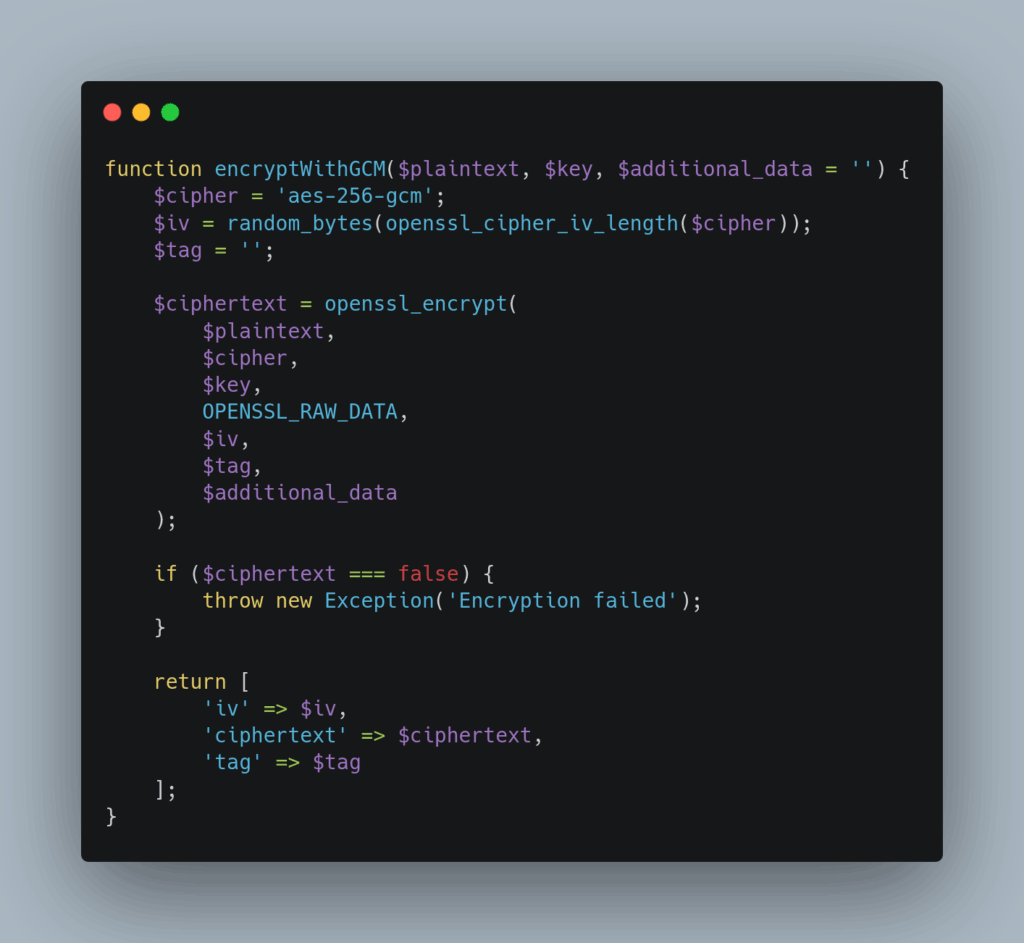
For environments where GCM isn’t available, CBC mode with separate HMAC authentication provides strong security:
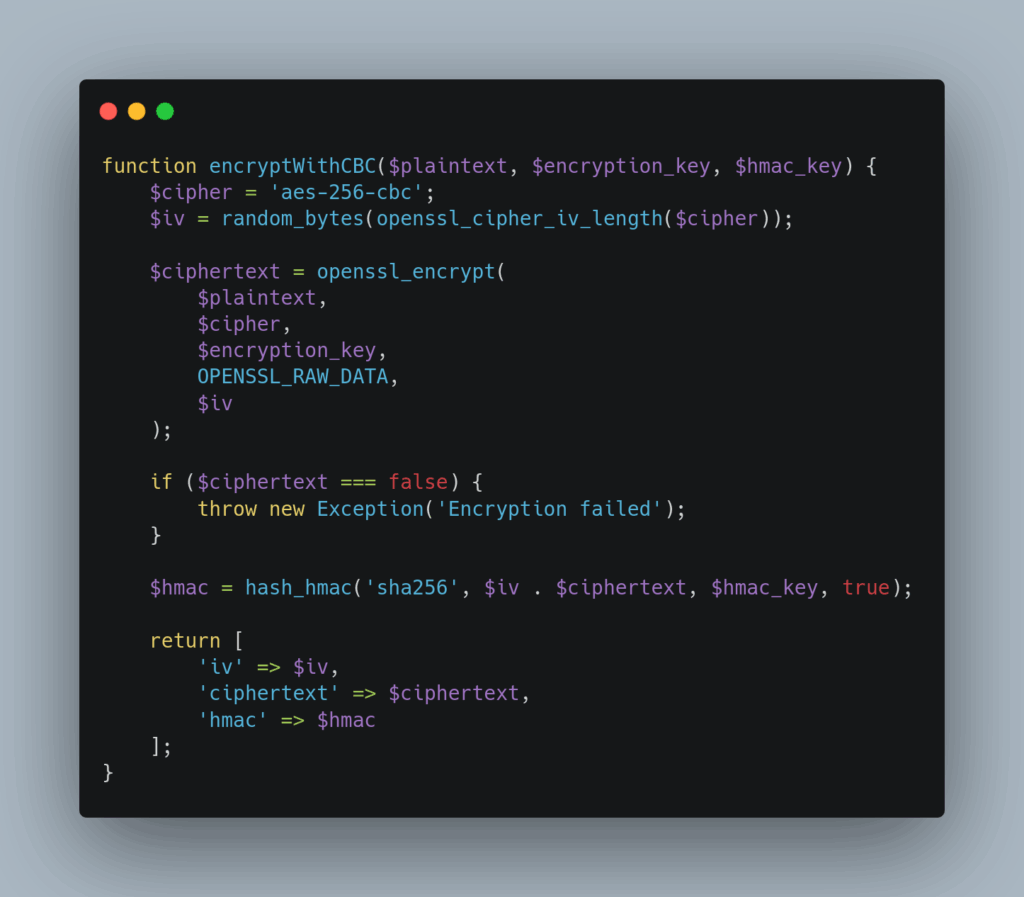
Choose GCM mode for new applications requiring authenticated encryption with good performance characteristics. Use CBC with HMAC for legacy compatibility or when GCM isn’t supported. Avoid ECB mode entirely, as it doesn’t provide semantic security and reveals patterns in encrypted data.
A robust encryption implementation requires proper error handling, secure parameter validation, and consistent data formatting. Here’s a simple complete encryption class.
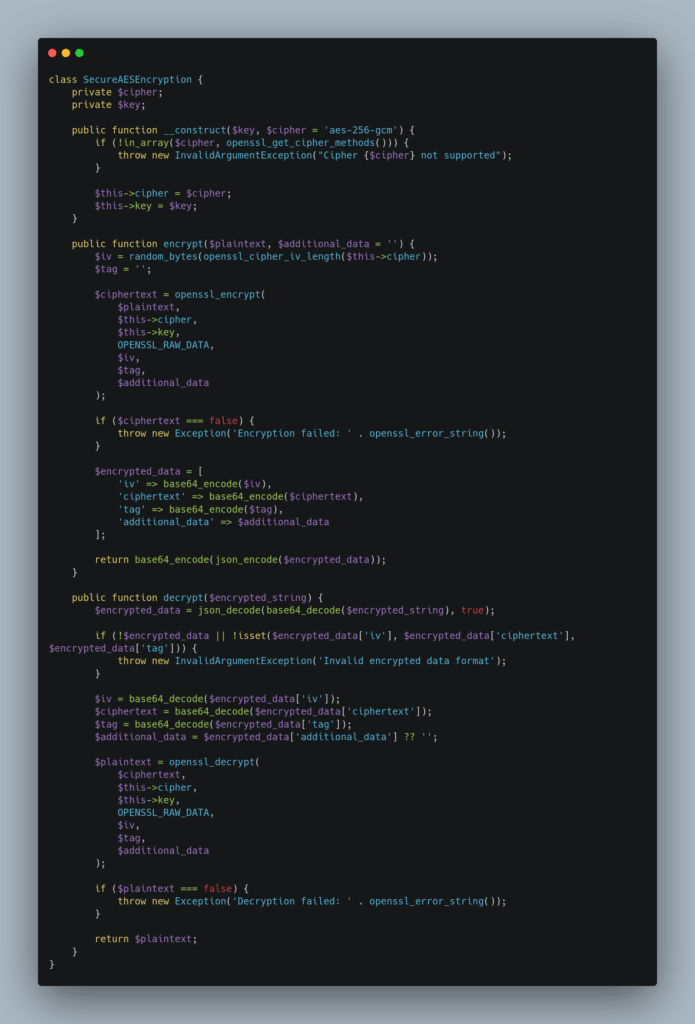
Proper key management extends beyond generation to include secure storage, rotation, and access control. Your key management strategy should separate encryption keys from encrypted data and implement appropriate access controls.
Store encryption keys in environment variables or dedicated key management systems rather than in your application code or database. Use key wrapping techniques when storing keys in databases, encrypting them with master keys stored separately:
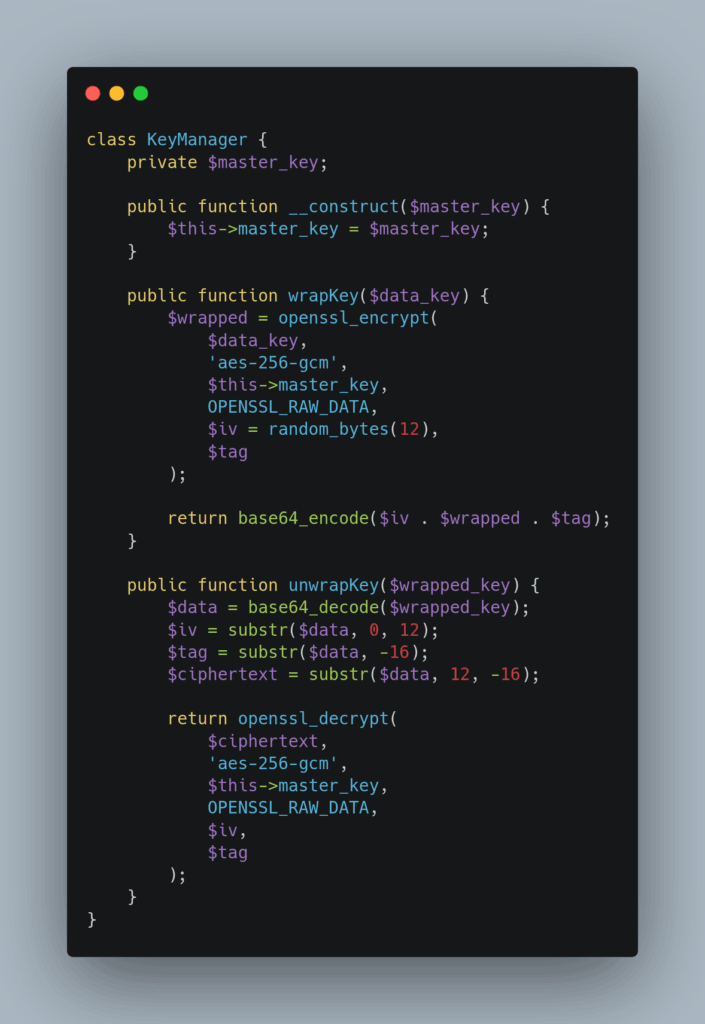
Implement regular key rotation to limit the impact of potential key compromise. Maintain multiple key versions to decrypt historical data while using new keys for fresh encryption operations.
Several common mistakes can undermine even well-intentioned encryption implementations. Understanding these pitfalls helps you build more secure systems.
Avoid openssl_random_pseudo_bytes(), which was deprecated in PHP 7.0. Always use random_bytes() for cryptographic random number generation, as it provides stronger security guarantees and doesn’t require checking return values for cryptographic strength.
Never reuse initialization vectors with the same key, as this can reveal information about encrypted data. Generate fresh IVs for each encryption operation using cryptographically secure random number generators.
Encryption without authentication leaves data vulnerable to tampering attacks. Always implement message authentication using either authenticated encryption modes like GCM or separate HMAC verification with encrypt-then-authenticate patterns.
When deriving keys from passwords, use proper key derivation functions like PBKDF2 or Argon2 with high iteration counts and random salts. Avoid simple hashing functions like MD5 or SHA-1 for key derivation.
Here’s a complete simple working example that demonstrates secure AES encryption:
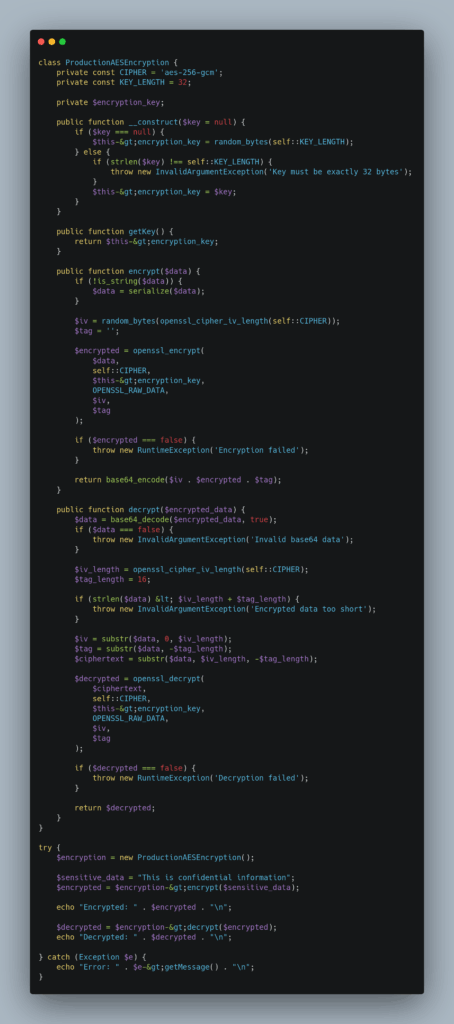
Getting AES encryption right in PHP doesn’t have to be complicated. The code above handles the important stuff – proper key generation, secure modes, and authentication – so you can protect your data without second-guessing yourself.
Just remember the basics: use random_bytes() for keys and IVs, stick with GCM mode when possible, and never skip authentication. Use this as a starting guide, but don’t stop here – study up on cryptography best practices and keep learning. Security isn’t something you set and forget.